23 KiB
Users
Linux is a multi user operating system.
For an end user's perspective this means we can have multiple accounts on one machine.
For example, one for each member of your household or company.
User can log in, out or switch accounts when seated at the computer or do multiple simultaneous logins via ssh or remote desktop software.
From a more internal point of view, Linux uses different accounts to do perfrom different tasks on the system. These accounts are often called system accounts.
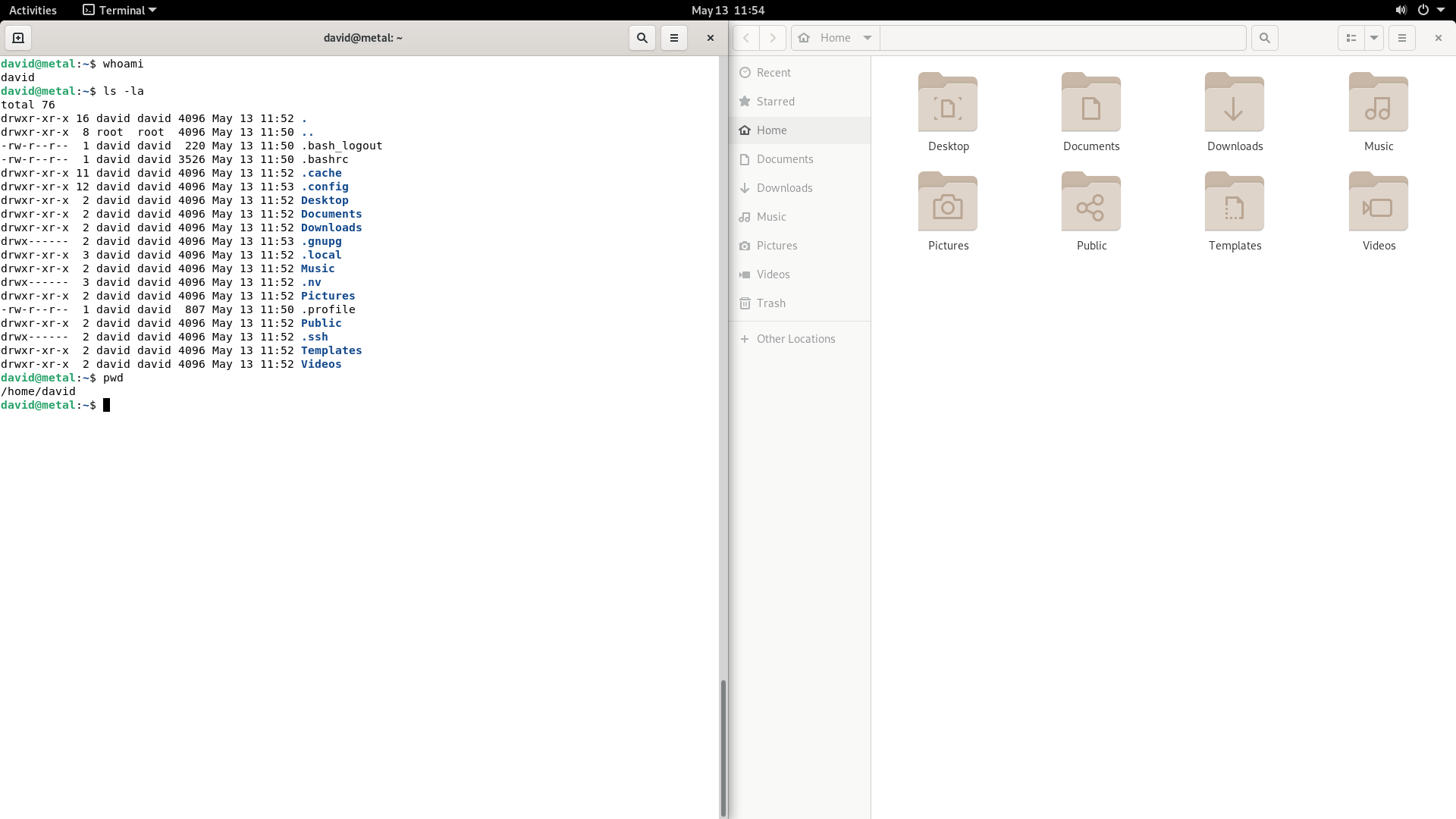
We can list all know accounts with the following command.
waldek@debian:~$ cat /etc/passwd | cut -d ":" -f 1
root
daemon
bin
sys
sync
games
man
lp
mail
news
uucp
proxy
www-data
backup
list
irc
gnats
nobody
_apt
systemd-network
systemd-resolve
messagebus
systemd-timesync
sshd
waldek
systemd-coredump
waldek@debian:~$
Accounts are nothing more than a correctly defined line in a text file! We can add and remove accounts as we please but luckily there are some tools to help us.
Adding and removing users
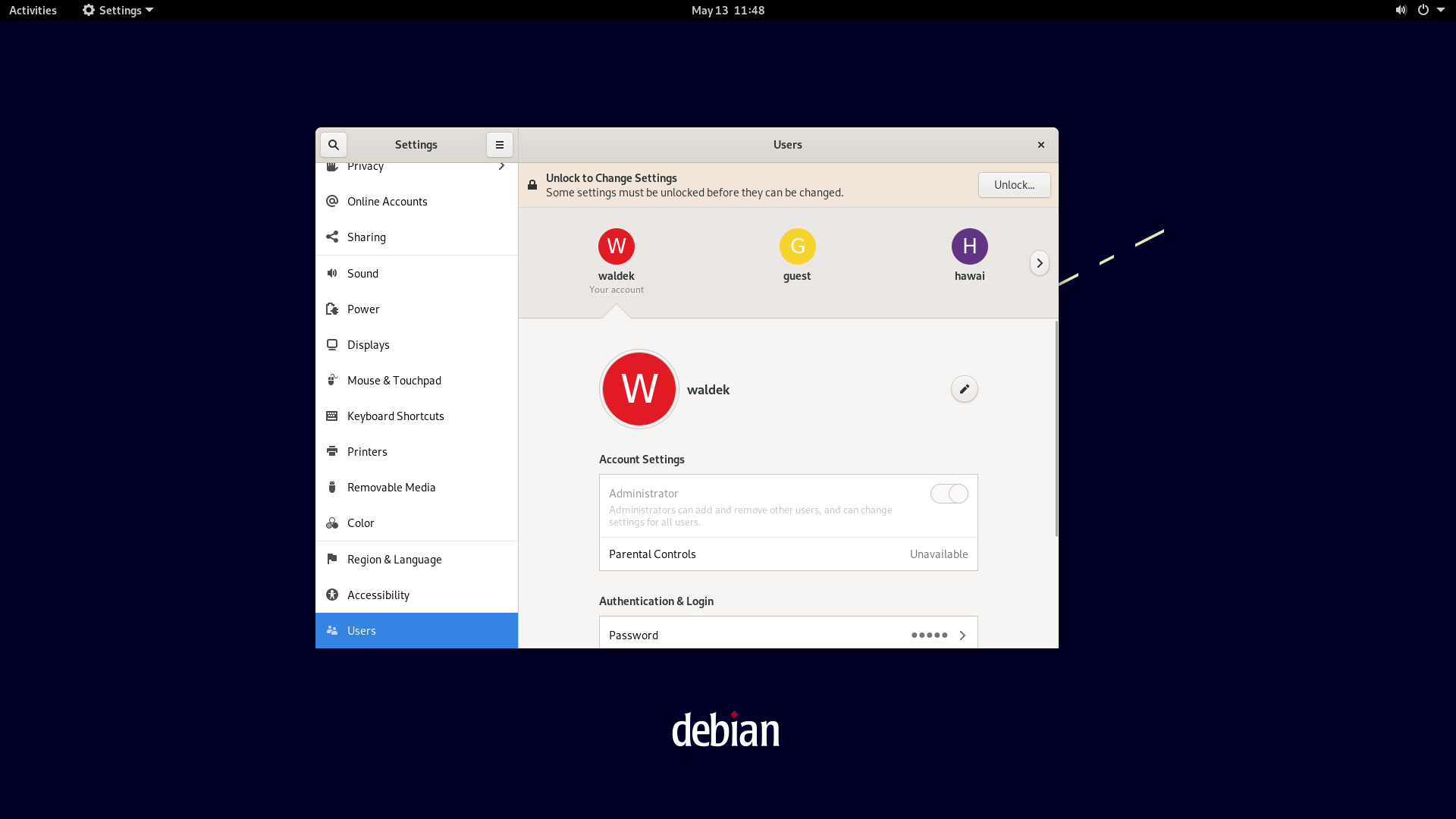
GNOME
In the gnome activities window we can search for add user and when we launch the program we'll see the dialog below.
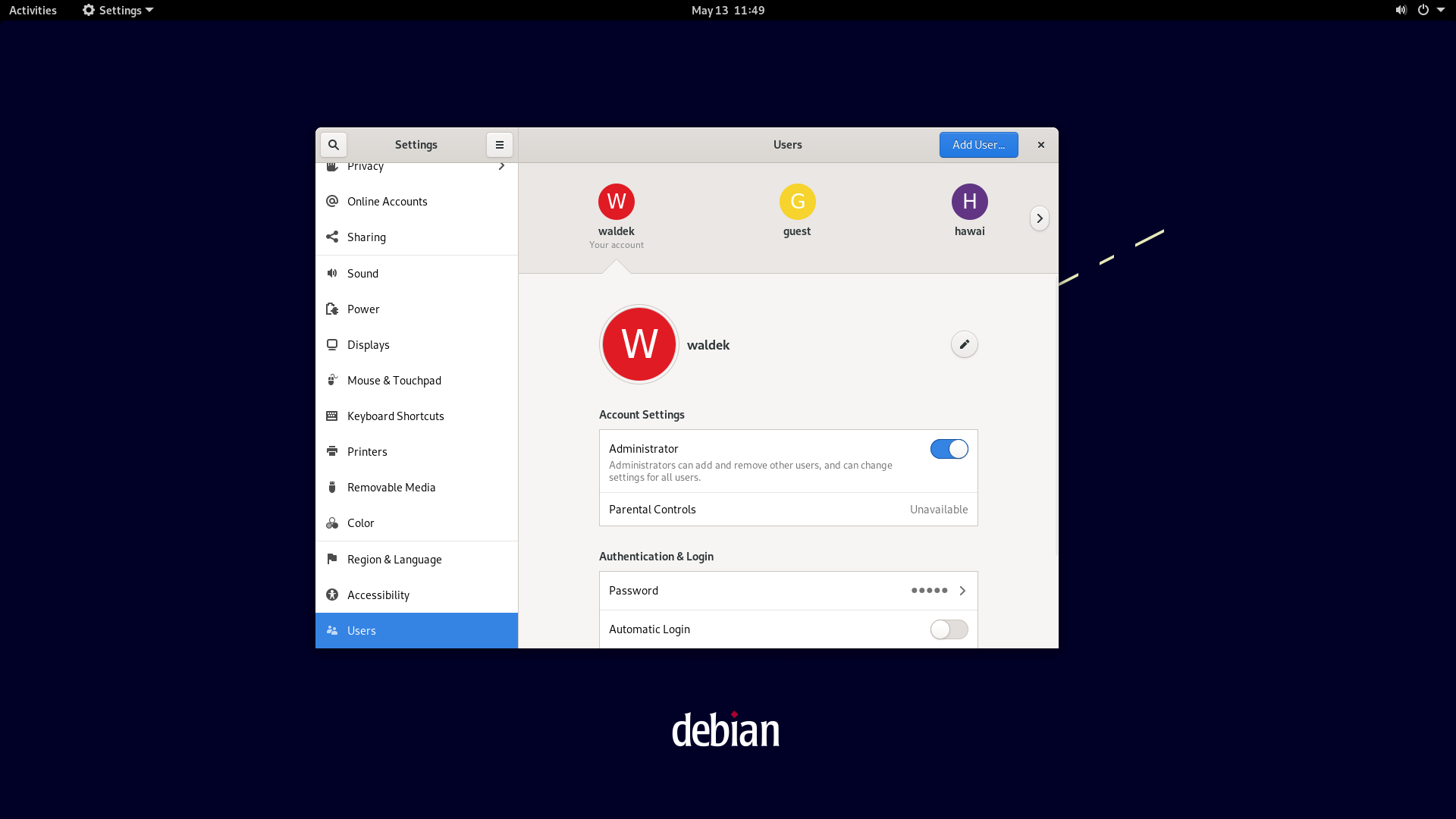
As adding a user is quite invasive to the system we need to prove we have the administration rights to do so.
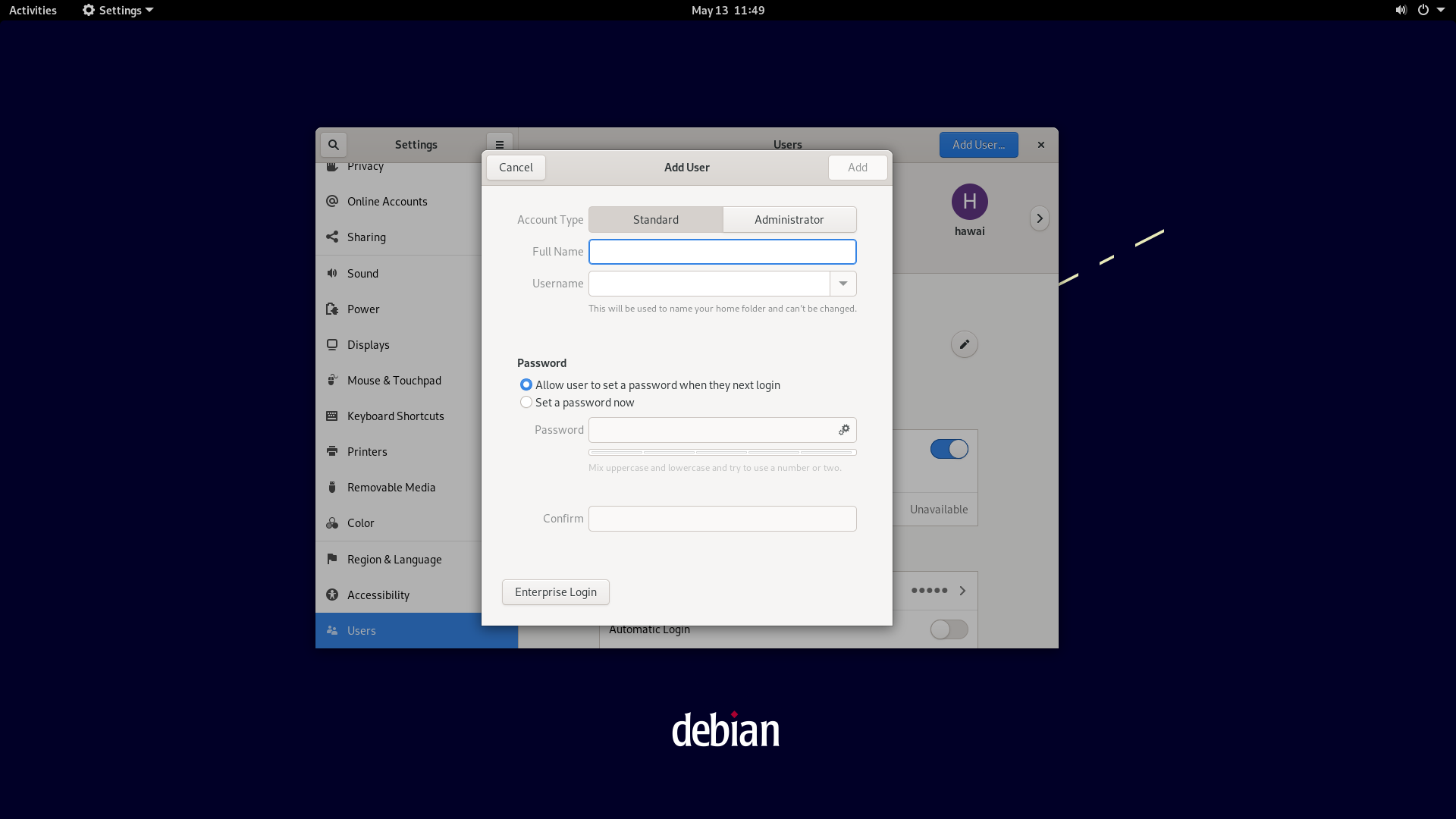
Now we can add a user.
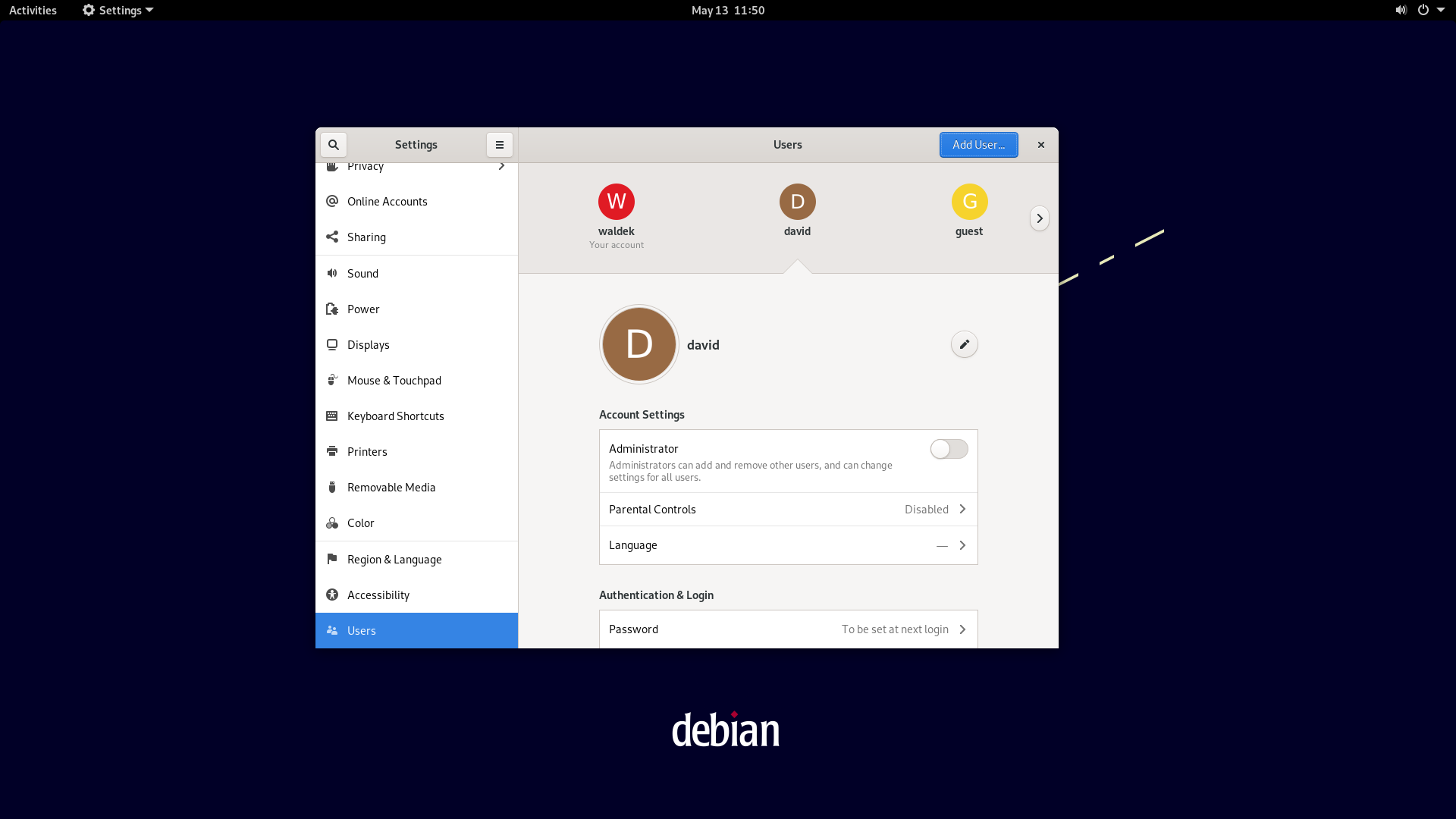
Done!
Now we can verify the account's existence by logging in.
Or via the command line.
waldek@metal:~$ su david
Password:
david@metal:/home/local/waldek$ tail -3 /etc/passwd
nvpd:x:125:137:NVIDIA Persistence Daemon,,,:/var/run/nvpd/:/usr/sbin/nologin
_flatpak:x:126:138:Flatpak system-wide installation helper,,,:/nonexistent:/usr/sbin/nologin
david:x:1005:1005:david,,,:/home/david:/bin/bash
david@metal:/home/local/waldek$
We can also remove a user via the graphical interface.
command line
This why you're here no?
To learn how to manager a Linux system like a pro.
So let's look into how to add and remove users via the command line.
As it's an administrative task we'll need to prove we have to right to do so.
This implies the use of sudo.
waldek@debian:~$ sudo add
addgroup addpart add-shell adduser
waldek@debian:~$ apropos adduser
adduser.conf (5) - configuration file for adduser(8) and addgroup(8) .
adduser (8) - add a user or group to the system
waldek@debian:~$ sudo adduser
[sudo] password for waldek:
adduser: Only one or two names allowed.
waldek@debian:~$
The adduser program takes one or two arguments.
The behaviour changes quite dramatically depending on the number of arguments.
When you give one argument, the program will add a user to the system.
When using two arguments the program will add a user to a group.
waldek@debian:~$ sudo adduser ilies
Adding user `ilies' ...
Adding new group `ilies' (1001) ...
Adding new user `ilies' (1001) with group `ilies' ...
Creating home directory `/home/ilies' ...
Copying files from `/etc/skel' ...
New password:
Retype new password:
passwd: password updated successfully
Changing the user information for ilies
Enter the new value, or press ENTER for the default
Full Name []:
Room Number []:
Work Phone []:
Home Phone []:
Other []:
Is the information correct? [Y/n]
waldek@debian:~$ tail -1 /etc/passwd
ilies:x:1001:1001:,,,:/home/ilies:/bin/bash
waldek@debian:~$ su ilies
Password:
ilies@debian:/home/waldek$
If we want to add ilies to the group of administrators we can use the same program but with two arguments, first the user, then the group in question.
ilies@debian:~$ sudo apt update
[sudo] password for ilies:
ilies is not in the sudoers file. This incident will be reported.
ilies@debian:~$ exit
exit
waldek@debian:~$ sudo adduser ilies sudo
Adding user `ilies' to group `sudo' ...
Adding user ilies to group sudo
Done.
waldek@debian:~$ su ilies
Password:
ilies@debian:/home/waldek$ sudo apt update
[sudo] password for ilies:
Get:1 http://security.debian.org/debian-security bullseye-security InRelease [44.1 kB]
Hit:2 http://deb.debian.org/debian bullseye InRelease
Get:3 http://deb.debian.org/debian bullseye-updates InRelease [39.4 kB]
Get:4 http://security.debian.org/debian-security bullseye-security/main Sources [120 kB]
Get:5 http://security.debian.org/debian-security bullseye-security/main amd64 Packages [146 kB]
Fetched 350 kB in 0s (902 kB/s)
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
1 package can be upgraded. Run 'apt list --upgradable' to see it.
ilies@debian:/home/waldek$
ilies is now a user account with full administrator rights!
An important detail you should know is that a user's groups are only loaded upon login.
This has as a side effect that when you add a user to a group, they need to log out and back in order for the changes to take effect.
There are tricks to bypass the behaviour though but I must say I always log out and back in myself.
Removing a user is done with the deluser program.
waldek@debian:~$ sudo deluser ilies
Removing user `ilies' ...
Warning: group `ilies' has no more members.
Done.
waldek@debian:~$ tail -1 /etc/passwd
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
waldek@debian:~$ grep ilies /etc/passwd
waldek@debian:~$ su ilies
su: user ilies does not exist or the user entry does not contain all the required fields
waldek@debian:~$
It's worth pointing out that both adduser and deluser are scripts.
We can verify this as follows.
waldek@debian:~$ file $(sudo which adduser)
/usr/sbin/adduser: Perl script text executable
waldek@debian:~$ file $(sudo which deluser)
/usr/sbin/deluser: Perl script text executable
waldek@debian:~$ head $(sudo which deluser)
#!/usr/bin/perl
# deluser -- a utility to remove users from the system
# delgroup -- a utilty to remove groups from the system
my $version = "3.118";
# Copyright (C) 2000 Roland Bauerschmidt <rb@debian.org>
# Based on 'adduser' as pattern by
# Guy Maor <maor@debian.org>
# Ted Hajek <tedhajek@boombox.micro.umn.edu>
waldek@debian:~$
The real heavy lifting is done by two other programs called useradd and userdel.
When writing your own scripts to add and remove users you should use these programs an not the perl scripts!
waldek@debian:~$ file $(sudo which useradd)
/usr/sbin/useradd: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=cddbc9a8bae8b6f626a47a2b5ed1ea76081eae6d, for GNU/Linux 3.2.0, stripped
waldek@debian:~$ file $(sudo which userdel)
/usr/sbin/userdel: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=cdf46de13b11b883951743d5652347a141bafba7, for GNU/Linux 3.2.0, stripped
Switching user
There are two different ways of switching user accounts or performing tasks as someone else: su and sudo.
su means switch user, while sudo means switch user and do.
sudo is a bit more modern but both have their utility.
So, some examples.
waldek@debian:~$ whoami
waldek
waldek@debian:~$ sudo whoami
root
waldek@debian:~$ sudo -u steve whoami
steve
waldek@debian:~$ sudo -u ilies bash
ilies@debian:/home/waldek$ whoami
ilies
ilies@debian:/home/waldek$ cd
ilies@debian:~$ pwd
/home/ilies
ilies@debian:~$
Above we can see that sudo is used to perform a task as an other user.
We can use this to launch single commands but also to launch a bash shell.
A more classic way to switch identity is to use su.
Below you can see the difference between a simple su call and with the - argument.
The difference is subtle but quite important.
Have a read of the man su for more information.
waldek@debian:~$ su ilies
Password:
ilies@debian:/home/waldek$ whoami
ilies
ilies@debian:/home/waldek$ pwd
/home/waldek
ilies@debian:/home/waldek$ exit
exit
waldek@debian:~$ su - ilies
Password:
ilies@debian:~$ pwd
/home/ilies
ilies@debian:~$ whoami
ilies
ilies@debian:~$
For the lazy...
-, -l, --login
Start the shell as a login shell with an environment similar to a real
login:
o clears all the environment variables except TERM and variables
specified by --whitelist-environment
o initializes the environment variables HOME, SHELL, USER, LOG‐
NAME, and PATH
o changes to the target user's home directory
o sets argv[0] of the shell to '-' in order to make the shell a
login shell
Groups
Groups are a second fundamental concept of any Linux distribution.
Every user has a primary group, most of the time the same name as their user account, and none/one/more secondary groups.
These groups can be made by us or by the distribution.
For example, sudo is the group that all administrators need to be a member of.
A few examples above I added ilies to the sudo group.
Once this was done, and ilies logged back in, he could perform administrative tasks.
adduser is used with two arguments to add a user to a group.
To create or delete groups we use addgroup and delgroup.
An example:
waldek@debian:~$ groups
waldek cdrom floppy sudo audio dip video plugdev netdev
waldek@debian:~$ su - ilies
Password:
ilies@debian:~$ groups
ilies
ilies@debian:~$ exit
logout
waldek@debian:~$ sudo addgroup friends
[sudo] password for waldek:
Adding group `friends' (GID 1003) ...
Done.
waldek@debian:~$ sudo adduser ilies friends
Adding user `ilies' to group `friends' ...
Adding user ilies to group friends
Done.
waldek@debian:~$ su - ilies
Password:
ilies@debian:~$ groups
ilies friends
ilies@debian:~$
Just like a user account is just a line in a text file, the group definitions are the same.
waldek@debian:~$ tail -5 /etc/group
waldek:x:1000:
systemd-coredump:x:999:
steve:x:1001:
ilies:x:1002:
friends:x:1003:ilies
waldek@debian:~$ sudo adduser steve friends
Adding user `steve' to group `friends' ...
Adding user steve to group friends
Done.
waldek@debian:~$ tail -5 /etc/group
waldek:x:1000:
systemd-coredump:x:999:
steve:x:1001:
ilies:x:1002:
friends:x:1003:ilies,steve
waldek@debian:~$
And we can delete the group as follows.
waldek@debian:~$ sudo delgroup friends
Removing group `friends' ...
Done.
waldek@debian:~$ tail -5 /etc/group
ssh:x:111:
waldek:x:1000:
systemd-coredump:x:999:
steve:x:1001:
ilies:x:1002:
waldek@debian:~$ su - ilies
Password:
ilies@debian:~$ groups
ilies
ilies@debian:~$
Permissions
Unix like systems differ greatly from a Windows system because they are not just multi tasking but also multi user.
Users and groups imply permissions, meaning who is allowed to do what on a system.
Permissions are tied to a file system, either real or virtual, but can't exist outside of this context.
When we list the files in a directory, we can add the -l flag to see more information.
In the example below I create a file called helloworld and show it's details with ls -l.
waldek@debian:~$ touch helloworld
waldek@debian:~$ ls -l
total 0
-rw-r--r-- 1 waldek waldek 0 May 16 10:32 helloworld
waldek@debian:~$
Next up I create a directory to store my pictures in.
waldek@debian:~$ mkdir photos
waldek@debian:~$ ls -l
total 4
-rw-r--r-- 1 waldek waldek 0 May 16 10:32 helloworld
drwxr-xr-x 2 waldek waldek 4096 May 16 10:33 photos
waldek@debian:~$
The file and directory above points us to suite a bit of information. Let's break it down. The table below slices each individual element apart. The first column indicates the type of file. This can be a directory, link, block device, character device, among others. Have a look here for an elaborate explanation of all possible types in Linux.
| type | owner | group | others | nr links | owner | group | size | mod date | name |
|---|---|---|---|---|---|---|---|---|---|
| - | rw- | r-- | r-- | 1 | waldek | waldek | 0 | May 16 10:32 | helloworld |
| d | rwx | r-x | r-x | 2 | waldek | waldek | 4096 | May 16 10:33 | photos |
Octal number system
The octal number system is the most used one to represent permissions in Linux. At first it might me a bit confusing but it's not that complicated. You just have to know that:
- read is worth 4
- write is worth 2
- execute is worth 1
The sum of these permissions is the octal representation. Below is a little grid to help you understand.
| sum | 4 | 2 | 1 |
|---|---|---|---|
| 0 | - | - | - |
| 1 | - | - | x |
| 2 | - | w | - |
| 3 | - | w | x |
| 4 | r | - | - |
| 5 | r | - | x |
| 6 | r | w | - |
| 7 | r | w | x |
Each file in Linux has three different permissions.
- for the owner of the file
- for the group of the file
- and for everyone who is not the owner nor in the group
In the example below I use chmod to change the mode or permissions of a file.
I highly encourage you to read the man chmod.
waldek@debian:~$ chmod 777 permission_test
waldek@debian:~$ ls -l permission_test
-rwxrwxrwx 1 waldek waldek 0 May 16 10:54 permission_test
waldek@debian:~$ chmod 000 permission_test
waldek@debian:~$ ls -l permission_test
---------- 1 waldek waldek 0 May 13 16:45 permission_test
waldek@debian:~$ chmod 123 permission_test
waldek@debian:~$ ls -l permission_test
---x-w--wx 1 waldek waldek 0 May 13 16:45 permission_test
waldek@debian:~$ chmod 640 permission_test
waldek@debian:~$ ls -l permission_test
-rw-r----- 1 waldek waldek 0 May 16 10:54 permission_test
waldek@debian:~$
When searching or files we discovered that we don't have the permission to read certain files, and now we know why that is! A small specific example.
waldek@debian:~$ file /etc/shadow
/etc/shadow: regular file, no read permission
waldek@debian:~$ cat /etc/shadow
cat: /etc/shadow: Permission denied
waldek@debian:~$ ls -l /etc/shadow
-rw-r----- 1 root shadow 1001 May 13 13:49 /etc/shadow
waldek@debian:~$ whatis shadow
shadow (5) - shadowed password file
waldek@debian:~$
As administrator we do have the right to read this file.
So we can add sudo before the command to peek into the file.
waldek@debian:~$ sudo tail -2 /etc/shadow
steve:$y$j9T$UHjx5oOFKyFR6VMY6y1IB/$EnLPe41c46wW9xN.6oKNUhHw2XH4xchlxb8w7k2T853:19125:0:99999:7:::
ilies:$y$j9T$5ykW1sIfDSOFUbaFEcS6i0$/r73taI9vEcXNuMGw.3evLqhWDuPTVaC1dK6wjmpTb2:19125:0:99999:7:::
waldek@debian:~$
What on earth are this lines?
Well, those are the passwords of your user accounts which are stored in the shadow file format.
Historically they where plain text but now they are hashed.
Don't forget you can read up about them in your terminal with man shadow, man passwd.
waldek@debian:~$ whatis passwd
passwd (5) - the password file
passwd (1) - change user password
passwd (1ssl) - compute password hashes
waldek@debian:~$ man 5 passwd
Now is a good time to point out the manual sections.
The manual for the passwd file and program are not the same.
We can read the file manual with man 5 passwd and the program manual with man 1 passwd.
More information of the sections can be found via man man where the table below comes from.
| section | description |
|---|---|
| 1 | Executable programs or shell commands |
| 2 | System calls (functions provided by the kernel) |
| 3 | Library calls (functions within program libraries) |
| 4 | Special files (usually found in /dev) |
| 5 | File formats and conventions, e.g. /etc/passwd |
| 6 | Games |
| 7 | Miscellaneous (including macro packages and conventions), e.g. man(7), groff(7) |
| 8 | System administration commands (usually only for root) |
| 9 | Kernel routines [Non standard] |
Changing ownership
Each file or folder in Linux has one owner and one group.
When you create a new file or folder, the owner will be you and the group will be your primary group.
Most of the time this will default to your username for both user and group.
We can however change the owner and the group of a file of folder.
This is done with chown, ch(ange)own(ership).
Let's try this out.
waldek@debian:~$ touch waldek_file
waldek@debian:~$ ls -l
total 0
-rw-r--r-- 1 waldek waldek 0 May 16 14:37 waldek_file
waldek@debian:~$ tail -1 /etc/passwd
ilies:x:1002:1002:,,,:/home/ilies:/bin/bash
waldek@debian:~$ chown ilies:ilies waldek_file
chown: changing ownership of 'waldek_file': Operation not permitted
waldek@debian:~$ su - ilies
Password:
ilies@debian:~$ cd /home/waldek/
ilies@debian:/home/waldek$ ls
waldek_file
ilies@debian:/home/waldek$ chown ilies:ilies waldek_file
chown: changing ownership of 'waldek_file': Operation not permitted
ilies@debian:/home/waldek$ exit
logout
waldek@debian:~$
No matter who we are we can't change the ownership of this file!
We can however perform this action as administrator.
Why is this so?
It would be a pretty big security issue if I could just claim files owned by ilies or vice versa.
So, with sudo we can do it as follows.
waldek@debian:~$ ls -l
total 0
-rw-r--r-- 1 waldek waldek 0 May 16 14:37 waldek_file
waldek@debian:~$ sudo chown ilies:ilies waldek_file
waldek@debian:~$ ls -l
total 0
-rw-r--r-- 1 ilies ilies 0 May 16 14:37 waldek_file
waldek@debian:~$ echo "hello world" > waldek_file
-bash: waldek_file: Permission denied
waldek@debian:~$ sudo chown ilies:waldek waldek_file
waldek@debian:~$ ls -l
total 0
-rw-r--r-- 1 ilies waldek 0 May 16 14:37 waldek_file
waldek@debian:~$ echo "hello world" > waldek_file
-bash: waldek_file: Permission denied
waldek@debian:~$ sudo chmod 660 waldek_file
waldek@debian:~$ ls -l
total 0
-rw-rw---- 1 ilies waldek 0 May 16 14:37 waldek_file
waldek@debian:~$ echo "hello world" > waldek_file
waldek@debian:~$ cat waldek_file
hello world
waldek@debian:~$ su steve
Password:
steve@debian:/home/waldek$ cat waldek_file
cat: waldek_file: Permission denied
steve@debian:/home/waldek$
umask
When you create a new file of directory, there are created with default permissions according to the umask.
waldek@helloworld:~$ whatis umask
umask (2) - set file mode creation mask
waldek@helloworld:~$ umask
0022
waldek@helloworld:~$ touch new_file && ls -l new_file
-rw-r--r-- 1 waldek waldek 0 Jun 15 15:02 new_file
waldek@helloworld:~$ mkdir new_folder && ls -la new_folder
total 8
drwxr-xr-x 2 waldek waldek 4096 Jun 15 15:03 .
drwxr-xr-x 59 waldek waldek 4096 Jun 15 15:03 ..
waldek@helloworld:~$
The new_file has a octal permission of 644 and the new_folder 755.
I can change my umask as follows.
waldek@helloworld:~$ rm -r new_f*
waldek@helloworld:~$ umask 000
waldek@helloworld:~$ touch new_file && ls -l new_file
-rw-rw-rw- 1 waldek waldek 0 Jun 15 15:08 new_file
waldek@helloworld:~$ mkdir new_folder && ls -la new_folder
total 8
drwxrwxrwx 2 waldek waldek 4096 Jun 15 15:08 .
drwxr-xr-x 59 waldek waldek 4096 Jun 15 15:08 ..
waldek@helloworld:~$
The permissions changed!
The new_file now has a octal permission of 666 and the new_folder 777.
Do you see a pattern here?
The umask value is subtracted from the POSIX defined base permissions which are 666 for a file and 777 for a directory.
One more example to drive it home.
waldek@helloworld:~$ rm new_f*
rm: cannot remove 'new_folder': Is a directory
waldek@helloworld:~$ rm -r new_f*
waldek@helloworld:~$ umask 777
waldek@helloworld:~$ touch new_file && ls -l new_file
---------- 1 waldek waldek 0 Jun 15 15:11 new_file
waldek@helloworld:~$ mkdir new_folder && ls -la new_folder
ls: cannot open directory 'new_folder': Permission denied
waldek@helloworld:~$
Can you explain me why we get a Permission denied message?
Some of you might have noticed the umask returns 4 digits.
This is because there is an additional permission bit we have not covered yet.
If you want to dig into it I suggest this page on the Debian wiki where I got the following quote from.
The first of the 4 octal digits which represent permissions contains the setuid and setgid bits. These can be used to override some of the defaults described above but it is not worth getting into details other than to note that the user private groups project collaboration idiom (see below) depends on the behavior of the setgid bit.
Advanced permissions
| type | value |
|---|---|
| sticky bit | 1 |
| setgid | 2 |
| setuid | 4 |
Essential programs
Below is a small list of often used programs when dealing with file permissions. I highly recommend you to read the manuals of each one.
| name | description |
|---|---|
id |
print real and effective user and group IDs |
chmod |
change file mode bits |
chown |
change ownership of a file |
umask |
set file mode creation mask |
chgrp |
change group ownership |
passwd |
change user password |
su |
run a command with substitute user and group ID |
sudo |
execute a command as another user |
Remote control of a server
TODO
History
Here you have a nice article on the history of remote shells. The two main ones are:
But today we don't use those anymore! We use ssh now!
SSH and SFTP
TODO
Bandit
You now have enough comprehension of Linux to play a wargame. Over at over the wire there are quite a few very good wargames to solidify your knowledge of the command line, the Linux kernel, web exploits, among others. We'll start off with bandit.
The Bandit wargame is aimed at absolute beginners. It will teach the basics needed to be able to play other wargames. If you notice something essential is missing or have ideas for new levels, please let us know!
It's a game you play over ssh which drops you in a bash shell where the goal is to find the password for the next level.
Once you find the password you can log out and back in as the next user.
The entire game revolves around permissions.
This is the cycle:
- log in as user
banditXto the server - find the hidden password for the user
banditX+1 - log out of the server
- save the password locally in a text file
- log in as user
banditX+1to the server - rinse, repeat and enjoy